It’s true! Your employees are one of the primary threats to your company’s cybersecurity. Though a majority of insider breach incidents aren’t reported, the number of cases increases each year. Any insider, including your existing and terminated employees, partners, and service providers can pose a threat to your organization’s sensitive data. The Verizon 2019 Data Breach Investigations report confirms that 34% of all breaches are caused by malicious or negligent employees.
In fact, these insider attacks cost businesses up to $8.76 million a year. Moreover, insider attacks are tough to spot as the attacker knows exactly where sensitive data is stored and what measures are taken to protect it. A 2018 Cost of a Data Breach Study reveals that it takes a firm an everage of 197 days to identify an insider breach and another 69 days to contain it.

Thus, it’s cheaper to take proactive measures to prevent such data breaches than to deal with the consequences. Employees can weaken your cybersecurity in the following ways:
- Using an unsecured network and data storage
- Using an old or weak password multiple times or using default admin passwords
- Not keeping up with system upgrades
- Accidentally installing malware
- Exposing sensitive information through phishing emails or messages
Here’s what you can do to brace your business against these internal threats:
1. Foster a security culture
A sustainable security culture will encourage all of your employees (not just the IT team) to take personal responsibility for protecting their organization from cyber threats. Further, it will convert cybersecurity into a lifecycle that will continue to generate returns in the long term.
Here’s how you can foster a security culture in your firm:
- Focus on the basics. For instance, make sure your employees use strong passwords and 2-factor authentication to boost the security of the system.
- Instill the concept that security is not just the IT team’s responsibility. Everyone in your organization should feel like a security person and take adequate steps to avert risks.
- Focus on employee awareness.
- Reward and recognize employees who adhere to the firm’s security policies.
- Build a security community that drives security culture, conducts timely meetings to discuss the latest threats, and offers one-on-one mentoring to employees.
Check out this infographic by Georgian Partners to build a strong security culture throughout the entire employ journey.
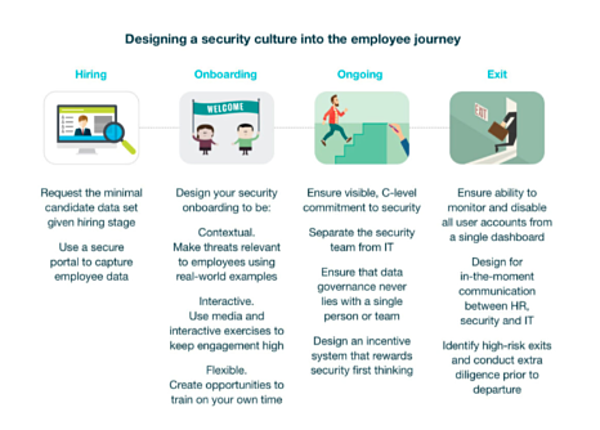
2. Spread awareness through security training for all employees
A Kaspersky report reveals that a majority of cybersecurity incidents occur because of low awareness among employees. For instance, an employee may simply not know what ransomware or malware is all about and may install an illegitimate app or respond to a phishing email.
Security training is a worthwhile investment as it saves you large sums of money and undue stress down the road. Involve your internal IT team or hire an external cybersecurity training professional who can develop a curriculum to train your employees to:
- Follow a rigid password policy
- Spot and manage phishing, spear phishing, reverse social engineering, and SMiShing attempts
- Watch out for malicious ads or apps
- Recognize the latest cyber threats, hacking attacks, and a variety of online scams
Run regular cybersecurity training and awareness programs to keep your employees updated on the latest in the field and foster a culture of good security practices.
3. Invest in an insider threat detection solution
An insider threat detection solution can detect security violations by verifying the identity of the employee trying to access the system, establishing patterns of life within the network, and monitoring anomalous on-screen activity. The system then warns you or the security officer of a violation, blocks questionable actions, and/or blocks a suspicious user altogether.
Therefore, it’s wise to invest in an insider threat protection solution like CimTrak, Forcepoint, Mimecast, or Securonix to protect your sensitive data and strengthen your firm’s cybersecurity system. These solutions use an AI-powered analytics-based approach that checks the files for suspicious access patterns, the network traffic for signs of unusual connections, and the data-protection logs for large data transfer, thereby detecting the threats operating inside the business.
Finally, install the open-source network intrusion detection system Snort to detect unusual activity on the network, reducing the risk of an employee absconding with your data.

4. Apply the principle of least privilege (POLP)
Under POLP, privileged access is allowed to certain employees on a case-by-case basis. For instance, depending on the system, some privilege assignments may be based on business functions like marketing, human resources, or IT. Other parameters like seniority, location, and trustworthiness may also be applied.
Applying the principle of least privilege to user accounts grants a limited set of privileges to employees. If users are only allowed to access data relevant to their work, the risk of accidental data leaks and data deletion will be significantly reduced.
5. Invest in a behavioral firewall
The highest probability of cybersecurity breaches lies with those who are exposed to sensitive data day in and day out. Hence, it’s a great idea to monitor their behavior and check for signs of discomfort and depression which could lead to such malicious acts.
Further, use a behavioral firewall like Preempt that understands and monitors the behavior of every employee who accesses the data. The firewall assesses the risk of every user and delivers adaptive actions to verify and eliminate threats.
6. Enforce a healthy bring your own device policy (BYOD)
Businesses are increasingly encouraging employees to use their own devices like laptops, tablets, or smartphones to work from home or while traveling. However, these devices are prone to cyberattacks too. Set up a rigid security policy and outline the rules and procedures people should follow when bringing their own devices to work.
- Your security policy should address risks like a possible data loss and a security breach. Prevent data leaks by deploying a mobile device management (MDM) system for all employee devices.
- Besides MDM, deploy a secure VPN to keep your data safe from attacks in case your employees need to access your network when away from the company premises.
- Mandate the use of updated security software on all devices.
- All locally-stored data should be regularly backed up.
- Track the progress of devices across multiple locations and wipe it of any sensitive material.
7. Encourage employees to use a secure VPN connection
Accessing organization data without the use of a secure VPN can significantly increase accidental insider threat risk. This is because employees often access a system using free or unsecured WiFi. If these connections are interrupted by malicious threat actors, any data accessed or transmitted is at the risk of exfiltration.
Therefore, businesses should consider investing in a premium VPN service that not only offers malware protection but also reduces the risk of a data leak. However, the cybersecurity team should be vigilant when employees use the VPN and watch out for malicious employees who can use these connections to access sensitive files and administrative controls.
Help grow the community by referring friends and family that could benefit from the product and get rewarded with $100. https://t.co/k3S9ptO0VQ pic.twitter.com/9IQ6WeTiEO
— Keap (@KeapGrowing) December 24, 2019
8. Create an employee off-boarding list
Determine the list of things you need to do (pertaining to security) when an employee leaves the organization. A few IT security precautions to be taken are mentioned below:
- Change all network and workstation passwords where the individual had access to.
- Secure all work files and folders.
- Deactivate all company user accounts and remote access accounts.
- Retrieve company laptops or devices.
Conclusion
Cybersecurity is increasingly becoming a struggle for organizations, especially when careless, disgruntled, and malicious employees have access to sensitive information. Overcoming these cybersecurity threats posed by employees can prove to be an excruciating and time-consuming process. However, it’s not as tough as it seems.
Use the tips shared in this post to minimize the threats posed by employees, either accidentally or with malicious intent.
About the author
Pratik Dholakiya is the Founder of The 20 Media, a content marketing agency specializing in content and data-driven SEO and PRmention, a digital PR agency. He regularly speaks at various conferences about SEO, Content Marketing, Entrepreneurship, and Digital PR. Pratik has spoken at 80th Annual Conference of Florida Public Relations Association, Accounting & Finance Show, Singapore, NextBigWhat’s UnPluggd, IIT-Bombay, SMX Israel, SEMrush Meetup, MICA, IIT-Roorkee and other major events. As a passionate SEO & content marketer, he shares his thoughts and knowledge in publications like Search Engine Land, Search Engine Journal, Entrepreneur Magazine, Fast Company, The Next Web, YourStory and Inc42 to name a few. Find him on Twitter @DholakiyaPratik.


